The Magnus Protocol ARG: Full Summary
An ARG – an Alternate Reality Game – is an interactive puzzle game that employs both real-world and online elements to tell a story with heavy player involvement. When Rusty Quill ran a Kickstarter to fund The Magnus Protocol, one of the most exciting stretch goals was that we would run our own extensive ARG. If you weren’t able to participate, or want to recap what happened, here is a summary of everything that happened, how it was made, and some behind-the-scenes insights from the Rusty Quill ARG team.
Please note that some resources and websites featured in the ARG are no longer available.
The ARG team
Alexander J Newall – Creator, Continuity Consultant, Copy writer
Jonathan Sims – Continuity Consultant
Sebastian Hutter – Co-Lead (Technical)
Jessica Anson – Co-Lead, (Administration)
April Sumner – Production Lead
Martyn Pratt – Technical Support
Tom Park, Hattie Quinlan, Callum Dougherty, Helen Gould – Supporting Staff
The timeline
24th March 2023 – ARG Brain Trust
12th April 2023 – Initial Meeting
15th September 2023 - ARG begins
Key ARG elements
- The O.I.A.R. is hiring
- Bonzoland shut down after the worst year ever, but their website is still up, if not entirely functional
- StangeHauntsUK, a Tumblr user, has made some posts regarding some familiar locations
- Colin Becher is having a bad time trying to understand the O.I.A.R.’s systemes (including “Freddy”)
- A DDR defector stumbled on dangerous information on The Magnus Institute
- The Magnus Institute burned down
The Vortex
It all began with The Vortex.
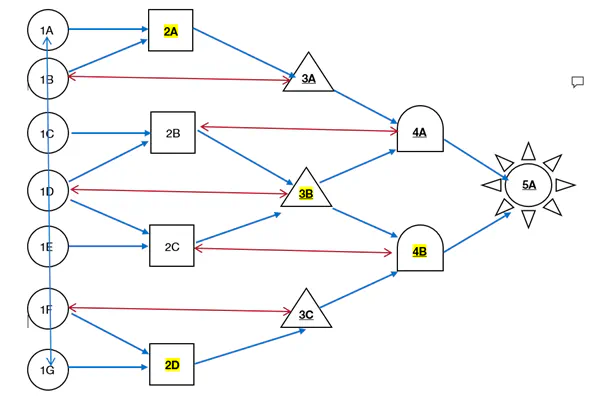
An original Alexander J Newall creation, the Vortex is the skeleton through which the ARG was created. 5 levels based on alchemically significant numbers, each interconnected and designed to draw in players and gradually ramp up in difficultly and complexity without allowing “lone-wolf” solvers, all the while revealing new information about the world of The Magnus Protocol. While the ARG was not something that was necessary to participate in to understand The Magnus Protocol, it was designed to contain a wealth of background story and context that would enrich any player’s listening experience.
While many ideas for what each of the individual Vortex puzzles could be were… ambitious (Alex was particularly keen on TV advertisements!), we worked together to build something that was viable for timelines, financially sensible, and accessible to a global audience. This meant focusing primarily on digital elements, but we were keen on in-person events as well to help make the ARG as large scale as possible. We settled on 5 in-person elements, and 12 digital elements, with the hope that by the time the in-person elements were scheduled to occur, the ARG-solving community would have grown enough to where the clues discovered in-person would be shared online, thereby keeping collaborative ARG momentum.
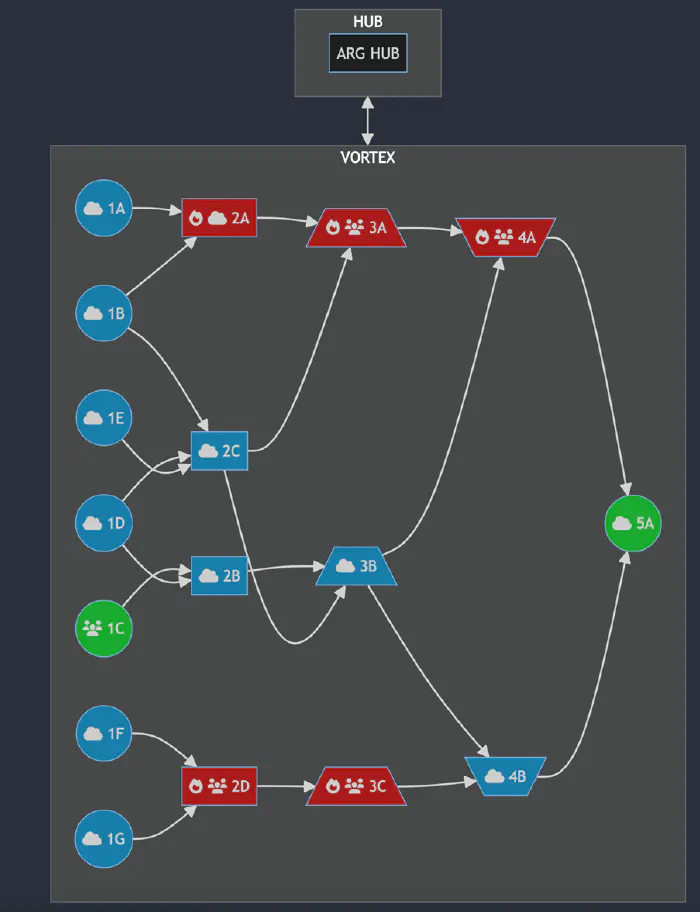
Alchemical symbols
Each puzzle needed two components to solve, and those components were hidden across different parts of the ARG. To reach Colin’s code repository, for example, players would need to find the QR code from the billboards in Manchester, and the code hidden in the O.I.A.R YouTube video ad. With that in mind, an important question became how to tie those components together. A component of a solve was often a time and date, or a password and URL, and we didn’t want to leave players unsure which key fit which lock, so to speak.
The answer lay in using alchemical symbols to pair ARG elements. Alchemy features within the world of The Magnus Protocol and many eagle-eyed fans have already spotted the alchemical symbols floating in the background of various promotional images. Some of the symbols used were arbitrary; simply a red string for players to follow, while others held a deeper meaning – for example, the day/night alchemical symbol was attached to the Bonzoland website, which, by day, was an innocuous enough website for a dead amusement park. At night, it changed to something much more sinister…
Players caught on to this quickly, helping them to sift through the extensive noise we generated and home in on the key components they needed to move forward.
Puzzles and solutions
Level 1
In ARG terms, Level 1 comprised of 7 ‘rabbit-holes’ – the first media artifact, website, contact, or puzzle, designed to draw in players. These were spread across various media forms to help organically draw in the largest number of players possible. The theme for level 1 was primarily The Office of Incident, Assessment and Response; the O.I.A.R, a fictional branch of the civil service that players were about to become very familiar with. That said there were additional glitches and oddities that soon led to other strange places.
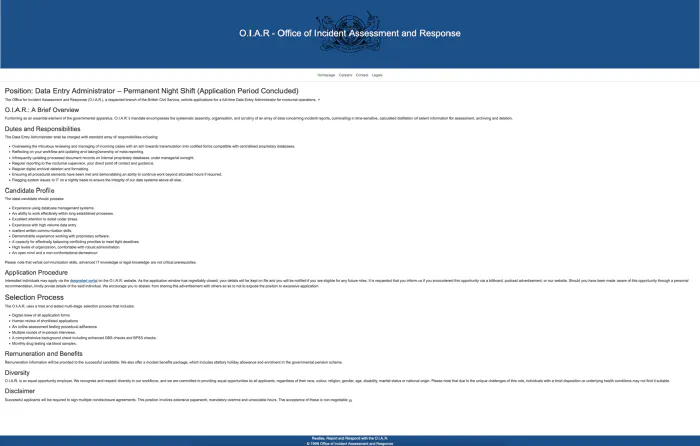
1A: A job advertisement for the O.I.A.R.
Concept:
The O.I.A.R are hiring – or were, at least. They have defunct job applications up on their website which list so much unappealing, corporate jargon that it would put off all but the most desperate applicant. They didn’t even bother to get the spelling right! At least that’s how it seemed initially, but those errors pointed to an inaccessible phone number…
Production:
This was a fairly simple puzzle to implement. Alex provided the copy – a horrendous corporate mess of uninviting duties & responsibilities and dubious selection processes that nobody would actually apply for (we hope). To find the ad, a player would need to send an e-mail to any O.I.A.R affiliated address, found amongst the level 1 puzzles, which would auto-respond and provide a link to the careers page of the O.I.A.R website, among other things.
Our initial idea was to have the job ad up on LinkedIn, but they immediately blocked our account due to “suspicious activity” which, let’s be honest, it absolutely was! Indeed was also vigilant. So we went with Plan C – utilising our own O.I.A.R website.
Linked To:
2A: The O.I.A.R phoneline 🜁
Puzzle:
After some deliberation, the puzzle team decided to hide the phone number players would be looking for in the form of typos. If a word had a typo in it, the number would be how many letters into that word the typo was.
For example: Dties is missing a u, which is the second letter in the word.
Players caught on fairly quickly, and were able to find the phone number in this manner.
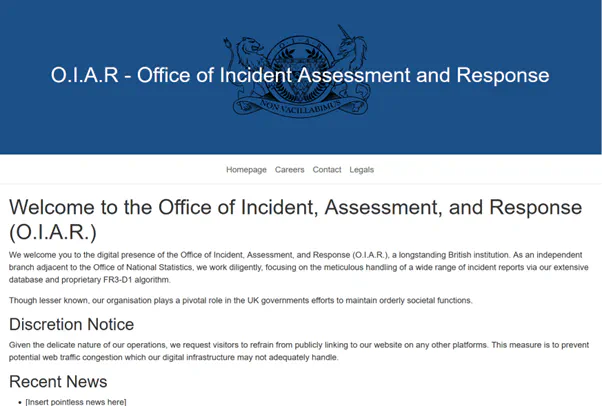
1B: The O.I.A.R Website
Concept:
The official website for the Office of Incident, Assessment & Response. Old, rarely updated, and uninviting.
Production:
This would be the hub for the Office of Incident, Assessment & Response; a website dotted with clues and red herrings, as well as links to other rabbit-holes. Alex provided the copy, and Sebastian put the site together. The idea was for it to look similar to a UK government website, but different enough to avoid any confusion with genuine official bodies since that could carry legal complications!
Linked to:
2A: The O.I.A.R phoneline 🜁
2C: DDR Defector’s Usenet Forum 🜶
Puzzle:
Since both 1A & 1B linked to the phoneline, we initially wanted to have two different puzzle solutions to lead players there. However, limitations on what we could do with the phoneline meant that we ended up having the phone number as a solution twice. In this case, we split up and hid the number across the image file names on the website.
The website also showed an error message when trying to fill in and send off the identification form. Hidden in the error console of the resulting page, players found a connection error for an nntp address, with some parts missing.
1C: Billboard Ads
Concept:
The O.I.A.R have leased billboards as part of their hiring initiative, but the QR code Colin has helpfully provided as part of their design has been hacked.
Production
The first part of the ARG that brought it into the real world: billboards. With Callum’s help we were able to lease two billboards in the Manchester area for two weeks. April designed them, and Sebastian provided the QR code that players could scan to take them to the next part of the ARG. We went for three designs: Rusty Quill themed, The Magnus Protocol themed, and O.I.A.R themed. Although this meant it wasn’t entirely ARG-themed, we couldn’t miss the chance to have some Rusty Quill billboards!


Links to:
2B: Colin’s code repository ☿
Puzzle:
The QR code led to the login page for the code repository when scanned. This was not much of a puzzle in itself; finding the billboards was more of a challenge in this instance. We did, however, end up creating a mini-puzzle to lead players to them, as the chances of a player happening upon them organically were slim within the limited time frame. For this mini-puzzle, players who had emailed freddie@oiar would receive one of two emails with a glitched out O.I.A.R. logo. The metadata of each revealed the coordinates to the billboards although some people wrongly construed them as triangulation points indicating they should instead break into a real prison! (This was NOT our intention and we had a few meetings to discuss what to do if anyone did attempt a jailbreak!) Thankfully the mini-clues worked in the end.
1D: YouTube Advertisement
Concept:
As part of their hiring initiative, the O.I.A.R released an advertisement on Youtube – but unbeknownst to them, a few things seemed to have gone awry…
Production:
In-universe, this video is posted by Colin Becher, the I.T. manager for the O.I.A.R.; in reality, April put together the video. As the mid-point of level 1, the video was the only element containing multiple clues.

Links to:
2B: Colin’s code repository ☿
2C: DDR Defector’s Usenet Forum 🜶
Puzzle:
Morse code hidden in the video audio gave the username and password for the code repository – players had difficult solving this puzzle, so it was duplicated in the Tumblr. See below for more details.
The IP address used to access the Usenet forum was also hidden in a few frames at the end of the video.
1E: Podcast Advertisement
Concept:
As part of the O.I.A.R’s hiring initiative, they released a podcast advertisement containing an email address and the subject line to include in order to submit your application.
Production:
How could we not do something with our podcast feed? This is the puzzle we knew would kickstart the ARG. The advertisement was uploaded specifically to The Magnus Archives podcast feed, only playing every so often for each listener. As this is where a huge majority of our fans would be listening anyway, it made for a great jumping in point. Copy was provided by Alex, with Hattie Quinlan lending us her voice. (We will return her voice to her a.s.a.p.)
Links to:
2C: DDR Defector’s Usenet Forum 🜶
Puzzle:
When players sent an email to the horrifically long and ugly email address: hr@office-of-incident-assessment-and-response.org.uk, they would receive an auto-response. The auto-response would contain a link to the O.I.A.R website, YouTube video and job advertisement. If they included the subject line ‘Job Application’, as directed in the podcast advertisement, they would receive a slightly different auto-response: one with a line of German at the bottom of the email. Hidden in the HTML of this particular email was a base64 encoded string that revealed the username and password of einsamenarr, a UseNet forum user. Players could then use this login to access a new area of the forum, and a new clue.

1F: Bonzoland Website
Concept:
In a change of pace, this was one of the two level 1 rabbit-holes that did not directly link to the O.I.A.R. Instead, this was a website for a defunct amusement park: Bonzoland. This is where players were introduced to Mr. Bonzo for the first time, and were both dubious, horrified and delighted in equal measure. Particularly when they were introduced to what we know as ‘Nightmare Mode Bonzo’…
Production:
The Mr. Bonzo website was a joint project – April provided all the assets and graphics, Alex provided the copy, and Sebastian put the website together. On the surface, it depicts what you could almost call a ‘cute’ version of Mr. Bonzo, but it doesn’t take much reading and diving in to start noticing that things aren’t quite right.

Links to:
2D: London Dead Hand Drop 🝰
Puzzle:
Hidden in the HTML of the ‘error’ image was a note repeating 3am, over and over. Sure enough, when players visited the Bonzoland website at 3am in their local time zone, they encountered Nightmare Mode. Creepy music played on top of a glitching image of Mr. Bonzo, and when run through a spectrogram, that music gave players a time and date: October 1st 2023.



1G: StrangeHauntsUK Tumblr
Concept:
The second rabbithole not directly tied to the O.I.A.R, strangehauntsuk is a blog written in-universe by someone interested in abandoned places. Two of those places just happen to be The Magnus Institute and Bonzoland, seemingly innocuous amongst the other posts but nonetheless still glitched like the O.I.A.R…
Production:
This was initially going to be a YouTube series, however time and resources meant that we moved to a Tumblr account. The initial idea stayed the same: 7 posts on creepy, abandoned places with 7 images that contained fragments of what would line up to reveal co-ordinates. Of the 7 of these posts, five related to real world locations and two of them related to in-universe locations: The Magnus Institute, and Bonzoland.
We were convinced that, next to the podcast advertisement, players would find this Tumblr account within 24 hours of posting, and thereby find O.I.A.R themed rabbit-holes and Mr. Bonzo themed rabbit-holes around the same time. We used ‘The Magnus Institute’ as a tag to link the post to the Magnus-verse, but not be too obvious about it. That was a little too successful; the Tumblr was left undiscovered for far longer than we had anticipated, meaning that when players finally did find it, they were dubious of its veracity. But it really was part of the ARG; conceptualised and written by April.
The Tumblr also ended up serving as a duplicate for the morse code found in the YouTube advertisement to help players along, in the form of morse code hidden in the header image.

Links to:
2D: London Dead Hand Drop 🝰
Puzzle:
7 posts on creepy, abandoned places with 7 images that contained fragments of what would line up to reveal co-ordinates.

Level 2
All the tech is FINE.
2A: O.I.A.R. Phoneline 🜁
Concept:
Using the information gleaned from 1A&B, players could call the O.I.A.R helpline, to receive a generic voicemail but if players called at a certain time, the voicemail changed to a numbers station containing a code which led them to a bookshop that seemed to be of interest. After a few days however, the voicemail suddenly became white noise. Almost as if someone did not want people digging any deeper…
Production:
We wanted to incorporate phonelines into the ARG, in some form or another. How that was going to happen changed over the course of planning. Initially, we wanted to go big and creepy; with players finding a real-world room full of phones that all rang at the same time or a string of phone boxes ringing at a designated time to lure players in a specific direction. Eventually, however, we decided it was logistically easier, cheaper and fairer to our global players to do something more accessible. So Martyn set up a new phone system, that he hosted in his living room, which players could call from almost anywhere. This acted as the O.I.A.R’s defunct and hacked voicemail.
Linked to:
3A: The Berlin Bookstore

Puzzle:
In an ode to The Magnus Archives and our previous ARG in October 2022, we decided to go for a numbers station puzzle to lead players to St. George’s English Bookshop. This was time coded; to ensure players weren’t trying to get there too early, we initially uploaded a voicemail pointing to the 22nd September, which changed to the numbers station at midnight on that date. A few days after the numbers station went live, and players had had enough time to decode it, we swapped that out for white noise. Many people assumed this noise contained a code itself but it did not, it only removed codes that were previously there…
2B: Colin’s Code Repository ☿
Concept:
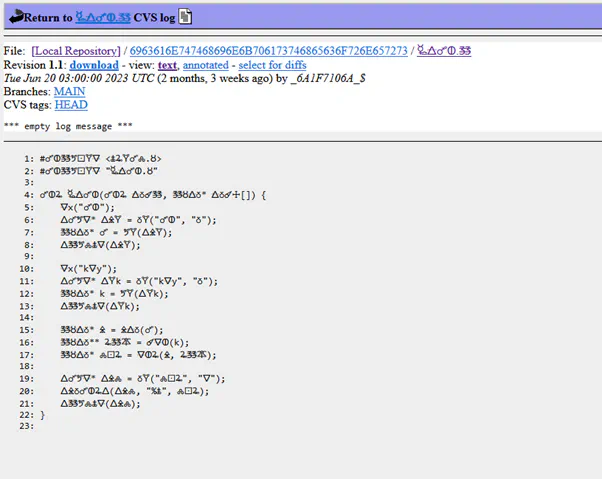
In his spare time, (or more accurately, on company time) Colin has built his own code repository for his personal code experiments using O.I.A.R resources. It seems a hacker discovered this repository and used it to communicate with players by providing them with a code that revealed the password for the documente.7z archive discovered in the DDR forum.
The code in question suddenly showed up in the repository, alarming Colin, who wasn’t entirely sure what to do with this new information, especially given that the code itself did not initially seem humanly readable.The solution of the puzzle was overwritten by someone else shortly after it was initially published. Perhaps the white noise culprit struck again? Either way, the players were tasked with figuring out what was going on with the code in the folder “6963616E747468696E6B70617374746865636F726E657273” (hex for icantthinkpastthecorners)
Production:
The initial idea here was to create our own puzzle in Github, which eventually turned into Sebastian creating custom cvs hosting and a code based around alchemic symbols.
Sebastian played around with different ciphers, eventually deciding to implement a Playfair cipher. He went with the Playfair cipher as it is a well-known cipher which still allows for enough complexity for a satisfying puzzle experience. The Playfair cipher needed an INPUT and a KEY, and produced an encrypted OUTPUT based on the Playfair rules.
He then had to choose a programming language which would have been around since at least the 90s. He eventually decided to use C, because the code is archaic, hard to read, and sounded like fun! (this last point was debatable!)
The alchemic cipher used the first letter of the meaning of a symbol to spell words out.
Linked to:
3B: The Magnus Institute Document Leak

Puzzle:
This puzzle was a Playfair cipher written in C, which was then translated to alchemical symbols to make it less readable and more challenging to crack. The players found the Playfair cipher written in C, a corrupted INPUT file, a KEY file and an OUT file. The goal was to find the INPUT of the program. To do this they had to first translate the C code and the KEY file from alchemical symbols into readable text, then reverse engineer the C code, and finally invert the Playfair cipher to retrieve the cleartext INPUT from the OUT file.
Besides the Playfair cipher, the site hosted other custom codes, all experiments by Colin but were initially thought as noise. The players were able to find the initial Linux Kernel 1.0 release, which listed the real names and email addresses of people involved in creating Linux – and immediately tried to send messages to emails found in the code. Fortunately, those email addresses weren’t active anymore!
They also found simple experiments by Colin in different programming languages. One of the experiments is a badly written, nearly unusable MUD client. The players were really interested in this piece of code. Their interest led to the creation of a small additional interim puzzle for the players – the telnet server / the mud server.
The mud server was discovered by players in the last week of the ARG as a mysterious hacker published an updated version of the mud client to colins code collection.
2C: DDR Defector’s Forum 🜶
Concept:
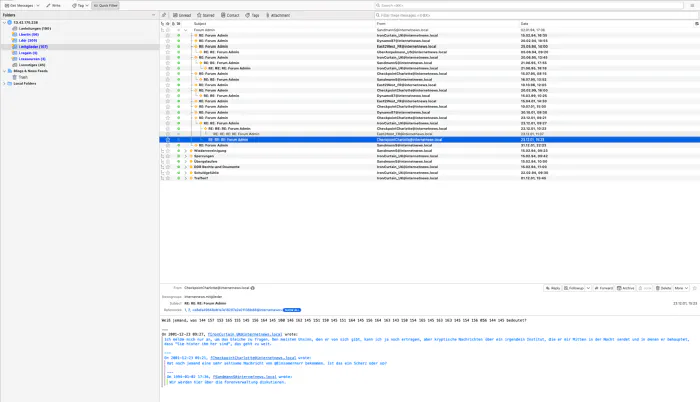
A private web forum for people who defected from East Germany/Soviet Union before the fall of the Berlin Wall. This would end up being the home of our ridiculous conspiracy nut, einsamenarr who somehow managed to stumble on some genuine documents from the destroyed Magnus Institute, and wanted a secure place to talk to people about it.
Production:
Although the DDR forum was, at its core, meant to be a plethora of noise and red herrings to distract players, it ended up becoming a focal point of the ARG for them. This wasn’t entirely surprising, given the many, many pages of copy provided by Alex, complete with detailed character bios. All of this content was created just for the ARG with every forum poster having their own likes, dislikes, personalities and agendas.
Linked to:
3B: The Magnus Institute Document Leak

Puzzle:
Once players had discovered the einsamenarr login details from level 1, they were able to access a member’s only section of the forum, where some of the characters were talking about einsamenarr sending them a strange DM. One of the characters posted what they had been sent – an email address coded in Octal, dokumente@freiheitentschluesseln.de
Sending an email to this address would yield an auto-response containing the now infamous dokumente.7z, einsamenarr’s secret repository of documents found in the TMI document leak.
2D: London Dead Hand Drop 🝰
Concept:
A secret copy of a corrupted database.
Production:
This was a group effort:
- Alex wrote the excel sheet
- Martyn created the glitched out picture of the statue
- Martyn put together the floppy discs
- Jess put together the book safes, and enacted the drop-off in London on 1st October


Linked to:
3C: Lady M’s PA ♃
Puzzle:
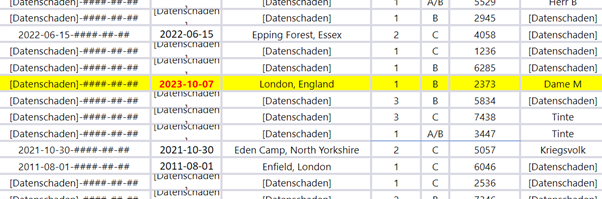
From the coordinates found in the strangehauntsuk tumblr, and the time and date found in Nightmare Mode Bonzoland, players were led to a ‘geocache’ location in London, where they would find a fake book safe hidden in a mini ‘library’ in Wapping. Once they managed to open the safe, they would find a floppy disc, and some destroyed instax photos. The latter was simply a red herring, but the former contained a csv sheet with a corrupted list of data including dates and times.
Level 3
Deeper strangenesses
3A; Bookshop Drop

Concept:
Einsamenarr took the precaution of leaving clues to some of what he had uncovered regarding The Magnus Institute in the form of a dead-hand geocache in a local bookshop.
Production:
Initially, we planned to use the cookbooks that einsamenarr posted on the Defector’s Forum for this puzzle. Players would find and recognise them from the forum, and discover coordinates inside, tying the two items together. This was scuppered by postal customs, however, who detained the post and we ended up going with an edited version of an old Berlin newspaper that players found between some cookbooks in the bookshop.
We worked with St. George’s English Bookshop in Berlin for this item, who were very helpful and engaged. (huge thanks to them!) We’d like to strongly encourage anyone who can, to visit the bookshop as both a show of thanks for their participation and because its genuinely an excellent shop in the area!
Linked to:
4A: The Magnus Institute Geocache 🜃
Puzzle:
We split up the co-ordinates players needed to find into 6 pairs (3x North, 3x West) and hid them in random places in the newspaper.
The coordinates were hidden the same way as planned with the books, and St. Georges Bookshop helped us by printing the documents (with very short notice!) and hiding them for us.
3B: The Magnus Institute Document Leak
Concept:
After solving the puzzles that gave players the dokumente.7z zip file (from the forum) and the password to that file (from the alchemic cipher), players gained access to some of the information that einsamenarr had taken from The Magnus Institute’s document leak.
Production:
We knew we needed to have a digital archive for the players to discover, so we implemented various bits and pieces for players to discover. Alex created the chdb.xls file – a database of experimental results relating to children at The Magnus Institute, which, whilst not essential for the ARG, was still a big “find” for the players. April created the (in)famous BonzoBucks, born from the Bonzo Bazaar shop discussions as detailed later. Finally, we needed a puzzle pointing the players to the date and time for the Magnus Institute geocache puzzle.
The puzzle was delivered in the form of a PDF containing 10 pages. When solved, it would give the players a unix timestamp which they could convert to GMT to find out when the Magnus Institute geocache was going to happen.

The players were very quick in discovering the binary code. Unfortunately, they didn’t connect the dots and it was looking like they wouldn’t convert it to a timestamp before the event happened.
This led us to first extend the telnet server with a new “SESSION” command which displayed the time when the player connected to the server as a unix timestamp. Again, players immediately discovered this; they also recognized the unix timestamp format but they didn’t quite connect the dots.
As the date for the geocache was getting closer and closer, we decided to send an email to anyone who had messaged dokumente@freiheitentschluesseln.de (einsamenarr’s email address that would auto-send dokumente.7z) with the same glitchy image used in the PDF but scaled up and converted to a gif with white noise running through it. The gif also hid the binary combinations of each of the PDF pages again. This time the players discovered the binary numbers, recognized that they are the same numbers as they got from the PDF and immediately jumped to the correct conclusion that they are looking at a unix timestamp.
Linked to:
4A: The Magnus Institute Geocache 🜃
4B: Bonzo Bazaar

Puzzle:
During the production of the timestamp puzzle, its contents and how it should work changed a few times. We wanted to do something with binary code as we hadn’t really worked with it yet, but it needed to be self-contained in the 7z file.
We ended up using a unix timestamp, which is 10 digits long.
These 10 digits were hidden in plain sight via an additional PDF :“Of the Generation of things”. The PDF contained a randomly selected alchemical text which started to become more and more corrupted the further the text progressed. The PDF was cut off at 10 pages.
We hid the timestamp in the form of a glitchy image in the corners of the PDF. Each corner of the PDF represented a bit. Whichever corner the glitchy image was placed in, that defined whether the bit was HIGH or LOW. The top left corner represents the bit for 8, top right for 4, bottom left 2, bottom right 1.
The Bonzo Bucks also contained a far simpler puzzle: hex codes that led to bonzobazaar.co.uk

3C: Lady M’s PA ♃
Concept:
After discovering that players are investigating and may find information about her through the clues they discovered at the dead drop, Lady M’s PA is stationed in Hyde Park and offers ARG players clues on condition that they cease all investigations into Lady M specifically.
Production:
We created 2 Proton email addresses: one for the players, and one for Lady M’s PA to send the email containing the clue from.
During gameplay we also had to create a third email address, again for the players, as Proton blocked the initial address due to suspicious activity. This happens when you have too many players accessing the same address from multiple locations!
Linked to:
4B: Bonzo Bazaar

Puzzle:
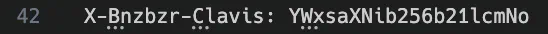
The PA on Lady M’s instructions (which was actually Alex on a call via a hand’s free set!) handed players paper printed with an email and password in Wingdings. Once converted back to plain text, this led to a Proton mail inbox, where players received an email at 7pm that same day. This email contained a separate email from an address connected to Bonzo Bazaar as an attachment. Hidden in the mail header of this attached email, players found the X-Bnzbzr-Clavis string, part of a keyed Caeser cipher. When decoded from base64, this revealed the phrase “allisbonzomerch”.
This was the key the players needed to unlock the password for the Bonzo Bazaar.
Level 4
4A: The Magnus Institute Geocache 🜃
Concept:
A VHS left undiscovered from the ruins of the burnt down Magnus Institute is found by players. When played, the contents show some kind of ritual being performed.
Production:
In order to provide raw digital footage, Alex forced his family on a day trip to Alderly Edge, to a specific cave he remembered. There they filmed the ritual with Alex’s mother and sister playing parts with Alex himself wearing a suit and gas mask. They were discovered by random members of the public who needed to be convinced it wasn’t a real ritual, since there have been numerous instances of people attempting black magic in the area over the years. All props and costume were provided by Alex after he explained “it’s okay, I have loads of weird sh*t just lying around we can use.”
This footage was then edited by April into a coherent piece of footage and overlays were added. This was provided to Martyn who recorded the footage via camcorder into VHS format, adding the code elements that were required at the end.
Martyn then provided the tapes to Alex who proceeded to burn them and break them without damaging the footage itself. He then wrapped them in brown paper bags and deposited them at the drop location, on the pavement outside a large austere Victorian building in Manchester with an adjoining burned out portion.
There was a brief complication in that the building seemed to be occupied by a secret group of scientologists who approached those brave enough to visit the site and invite them inside the derelict building. Thankfully players realised this was not part of the ARG and stayed outside.
Unfortunately for them, Alex was monitoring the site (having being spotted earlier as “Cool hat guy”) and so as the players moved to leave he yelled at them with a “we’re watching you” gesture before driving off without explanation. Her apologises for any excess terror he may have created.
Linked to:
5: The Magnus Institute Database 🜓
Puzzle:
Initially, we were going to use the items in the video as clues for the final puzzle, however when run through VHS it became difficult to see the items! So we went for alchemical symbols, linking back to the many, many uses of those symbols throughout the ARG. These would flash up after the initial ritual video in a specific order that would become relevant once players found the final piece of the puzzle in the Bonzo Bazaar website.
4B: Bonzo Bazaar

Concept:
A part of the remnants of the Bonzoland website, the Bonzo Bazaar shop was hidden behind an admin login after the items being sold started to become… weird.

Production:
This one was a lot of fun. The puzzle team sat down for a meeting dedicated to brainstorming cursed Mr. Bonzo merchandise ideas, based on things that would have been popular in the 90’s. There was a long list of ideas, but given time restraints and resources available, we ended up with the below.
Here’s some of the ones we left on the cutting room floor:
- Mr. Bonzo Tamagotchi (his head is the device)
- Mr. Bonzo Pez dispensers
- Inflatable Mr. Bonzo chair
- Inflatable Mr. Bonzo paddling pool
- Mr. Bonzo pogs
- Hungry Hungry Mr. Bonzo game
Martyn took these and created the.. delightful Bonzo Bazaar website, complete with 90’s style slow-loading images.
Linked to:
5: The Magnus Institute Database 🜓
Puzzle:
Once the players gained access to the Bonzo Bazaar shop, they immediately discovered 4 broken images on the website. These were in fact text files, each of them containing a part of a GPG encrypted file.
The players required the private key found in the TELNET server to decrypt this GPG file. Once decrypted the players were presented with a HTML file flashing the cinnabar symbol, and were redirected to the last puzzle website https://db.themagnusinstitute.org
5: The Finale 🜓
Concept:
The solves from 4A & 4B led to The Magnus Institute Database – or at least, that’s what players were led to believe. After inputting the alchemical symbols into the login page as denoted by the VHS footage, players’ browsers suddenly crashed, blue-screened and instead took them to a ‘Congratulations’ page on the O.I.A.R website, where they were informed that everything they had taken part in was DEFINITELY part of a recruitment drive. Nothing to see here. Everything is FINE. Here’s a reward, look at the shiny reward! TELL NO ONE.
Production:
We toyed with a few different ideas for the ARG finale, but in the end, this is where we landed, for multiple reasons which will become clear in the course of The Magnus Protocol series. Sebastian put together the 90’s style database website, including the fake-out bluescreen effect, and the O.I.A.R website complete with confetti at the end of the ARG.
Players were rewarded with a brand new The Magnus Protocol trailer, plus a merch drop a couple of days later.
Final Notes
As the ARG progressed, we needed to insert a few new puzzles to ensure that players would reach the correct solves in time for the planned in-person events. These are not all documented here, but you can find the source code – from the playfair cipher and the telnet server to every website – in our public Github repository: https://github.com/rustyquill/protocolarg
There were a large number of red herrings, and to put it simply, if something isn’t listed as a puzzle in this document, that’s what it was. For example: the Freddie contact box on the O.I.A.R website; the white noise audio voicemail on the phoneline; a vast majority of the DDR forum; the polaroids found in the book safe… all there to add flavour to the ARG!
We hope everyone enjoyed playing and although there are still mysteries to answer, rest assured The Magnus Protocol podcast should answer them all in due course!
– Jess & the ARG Team


